Organizations continue to cast their unprotected and sensitive data around while spending millions on cybersecurity to keep it protected and contained. The result is a cybersecurity crisis that cripples individuals, companies and nations. One replaceable technology is most at fault.

As the world grapples with a pandemic, organizations have increasingly been fighting a protracted and losing war against computer viruses. [1] Recent news informs us of a malicious file that can infect any Microsoft Windows machine, granting the cybercriminal remote access and there is currently no known fix. [2] So, what now? Just stare at our screens? Maybe just turn off our computers and pick up those needed groceries — hopefully the traffic system isn’t compromised. [3]
What we see play out every single day is the news of the lost battles — organizations, private and public, breached. Their data either stolen or locked up for ransom by powerful encryption, disrupting their operations, damaging reputations, stealing their precious intellectual property and costing millions to pick up the pieces. [4] Of course, we all pay as a society. Often it is the services we rely on that are disrupted and the data stolen is our data. [5] Organizations that could be spending precious resources on developing new cures, teaching our young or managing our critical infrastructure are forced to divert funds into a futile effort to defend and clean up, breach after breach.
At what point do we look outside of our box and notice that there are huge holes in our collective security strategies and that the fixes to these challenges are right in front of us?

The reality is that the cybercriminals have a fundamental advantage, an advantage so powerful that no amount of defense has proven truly effective. Like having the high ground, the topology of the digital battlefield favors the cybercriminals. That advantage is our stubborn reliance on a 1970s era technology for file sharing. The most common file sharing technology worldwide, by far, is a technology developed at a time when color television was beginning to overtake black and white, namely, the email attachment — and it’s killing us. In an age in which we are celebrating advances in artificial intelligence, internet of things and blockchain, we are sharing our precious data with the technological equivalent of an 8” floppy. As a result, with every file we send through email, we promote the most effective entry point to every one of our devices and the massive, unprotected and untraceable distribution of our data.

How can we possibly believe that we can protect ourselves while we throw our most sensitive data everywhere with total unprotected and untraceable abandon. We are truly our own worst enemies and the cybercrooks are laughing all the way to the bank.
What makes the current situation even more egregious, is that for years, a viable alternative to email attachments has been available. Cloud storage file share links from popular services like Box, Egnyte, MS One Drive, or Google Drive, are readily accessible to many workers. In some cases, even built into the most popular email services (O365, GSuite). File links provide a secure, efficient and purpose built means for sharing files through email. [6] Security features like encryption, authentication and access revocation, all missing with email attachments, are standard capabilities.
The most common file sharing technology worldwide, by far, is a technology developed at a time when color television was beginning to overtake black and white, namely, the email attachment — and it’s killing us.
The security benefits of file links over email attachments are many and immediate. Two key benefits are safe file preview and file containment.
Safe File Preview
File share links allow email recipients the ability to safely preview file content away from their devices. In the case of the aforementioned on-going and unpatched (as of this writing) Windows virus, remote preview wont expose the user’s device to the malicious code. From a safe distance, end users can determine if a particular file is relevant. No longer do they need to play email Russian roulette, open the file and hope that it doesn’t silently infect their device.
Data shows that, in a vast majority of cases, recipients don’t even need to download email attachments. Having the ability to preview, without download, meets the user’s requirements 88% of the time. Email attachment preview avoids attachment download and the concomitant dangers of file duplication, and malicious code execution — both problems posed by standard email attachment download. [7]
File Containment, Chain of Custody & Access Control
With a computer virus, like a biological virus, the ability to understand and trace the vector of an attack’s subsequent spread is critical to remediation. In the case of email attachments, the epidemiological / forensic effort made after a breach is incredibly difficult. Email attachments are unsecure and untraceable entities. Ascertaining which employees opened a malicious file attachment and tracing down the potential distribution of that file through email is an enormous undertaking because the email and its malicious file can be on any users’ multiple devices. Because the attached file is a self contained delivery mechanism, to defend the organization, every device must be protected or every copy of the email be found, prior to end user access. Given that for every worker, email attachments create a data sprawl problem of more than 55,000 file duplicates per year — no wonder the house is always on fire. [6]

Files that are delivered as email attachments do not self-replicate like standard email attachments do. By definition, a file link points back to a single file in a single location. Shutting down distribution of the malicious file becomes trivial by comparison, simply deny access to the file either through cloud storage access controls or firewall policy. Furthermore, cloud storage systems provide detailed audit records of who accessed and when — aka “chain of custody”. From this information, a detailed map of potential “infection” serves as the epidemiological data needed to take targeted and effective counter measures.

Adoption: getting workers to use cloud storage file links
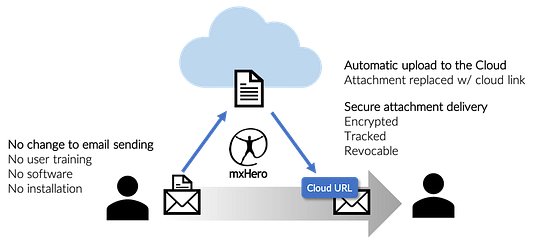
The vital advantages of sharing files through cloud storage file links are many and quantified. [6, 8, 9] But user adoption of sending file links rather than email attachments requires changing long held habits. The good news is that the ability to generate cloud storage links in email is becoming part and parcel of the most popular email applications, namely, Microsoft Outlook and Google Gmail. For even greater automation, technologies like Symantec’s Email Threat Isolation and mxHero’s Mail2Cloud platform ensure the email attachments are automatically uploaded to cloud storage for safe preview and secure delivery. These solutions work uniformly across every user device while requiring no end user involvement.
Closing
Email attachments are no longer adequate for today’s needs. Fifty years ago, the designers of email did not anticipate state sponsored espionage or the mass digitization of today’s workplace. Email is the modern inheritor of the letter, a role it serves so well that it has held its place as the primary means of communication on the Internet since the networks inception. But not all parts have adapted well to the realities of the current cyber landscape. Email attachments, for decades, have presented limitations and threats that increasingly create an unnecessary burden on society by threatening our individual privacy, diminishing the competitiveness of our industries, the security of our nation and even the health of our planet. [1, 9] With the rapid rise and adoption of cloud content storage, the modern alternative to email attachments has arrived. Now is time to say, “no” to email attachments and stop endlessly pushing the boulder up the hill.
Sources
- USA Cybersecurity Solarium Report, March 2020
- Microsoft Confirms Critical Windows 10 Exploit: Ongoing Attacks, No Fix Available
- Out on a Highway Run: Threats and Risks to ITSs and Smart Vehicles
- Cost of a Data Breach Report 2019
- 200M Records of US Citizens Leaked in Unprotected Database
- Our Dangerous Reliance On Email Attachments And What To Do About It
- On-Demand Partner Webinar: Archive Emails and Banish Attachments with Box + mxHero
- Containing Data Sprawl In The Work-At-Home Era of COVID-19 And Beyond
- Save the Planet: Replace Email Attachments With File Share Links

