While there is no denying that blockchain technology has brought transparency, security & reliability via the trustless, decentralized systems, nefarious players have found loopholes to penetrate the different security mechanisms that blockchains provide. To explore some of the vulnerabilities that have been exposed in blockchains, we first need to understand what constitutes the blockchain tech – cryptographically linked data structures, peer-to-peer networking, and consensus protocols. These weaknesses need to be fixed if the technology has to survive the onslaught of people with malicious intent. Before we move forward, the following table shows a comparison between the strengths & weaknesses of some of the popular consensus protocols being employed by blockchain technology.
 Software bugs & glitches
Software bugs & glitches
These can include anything from coding mistakes by developers, poor implementations of an underlying flaw in the cryptography routines. Even experienced programmers can make a mistake in putting together tried & tested cryptographic tools so that they are not secure. An example of this is a bug detected in the Bitcoin network in 2018 & revealed through Common Vulnerabilities and Exposures (CVE) report– the bug would have allowed an attacker to inflate the supply of Bitcoin by creating a new digital coin, thereby devaluing current bitcoins – keeping in mind that bitcoin has a fixed supply of 21 million. The bug was ultimately fixed, but not before creating a serious scare which could have shut down a portion of the bitcoin network. The other example signifies how subtle some of these glitches can be – the vulnerability evaded the cryptographic team of experts at Zcash for years. Eventually a cryptographer at the company uncovered the vulnerability where a parameter setup algorithm mistakenly produces extra elements that violated the soundness of the transaction proving system. The Sapling upgrade later last year fixed the issue on the network. More details on the issue could be found here.
Peer-to-Peer Network Vulnerabilities
An example of an attack on a P2P network is called the “eclipse attack.” Such an attack is orchestrated by someone who seeks to isolate a specific user (node) on a decentralized network. Rather than hijacking the whole network, the malicious player tries to control individual nodes which are in turn connected to other nodes. The blockchain connections are designed as such for efficiency where a node is connected to a select group of nodes & so forth. For example, the blockchain network node has 8 outgoing connections while Ethereum has 13. The attacker can fool the network into accepting fake information by carrying a double spend attack, whereby an isolated node is duped into thinking that transaction sent to them is valid although it has already been executed.
Consensus Protocol Loopholes
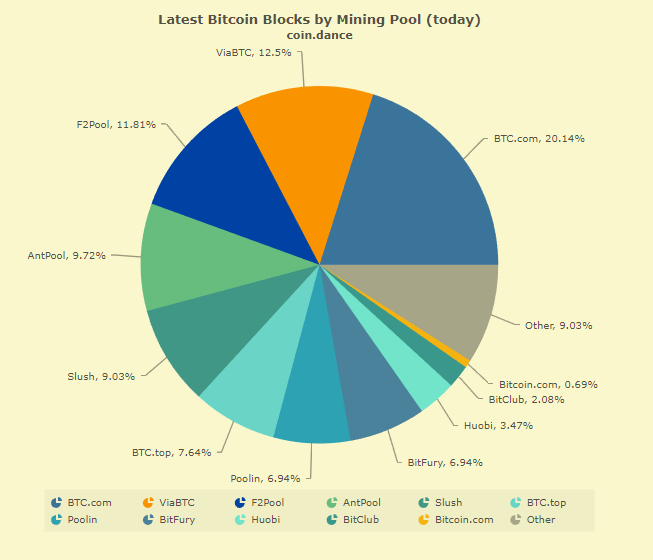
The most synonymous is the “51 percent attack” which occurs on a Proof-of-work blockchain when a group of rogue actors can take over more than 51% of the mining capacity of the network, thus taking control of the whole network. There has been talk about malicious actors launching such an attack ever since the network has existed. This looks even more likely with a few select companies mining for bitcoin (figure above) – although none has happened on the bitcoin blockchain so far. Bitcoin Gold, an off-shoot of the crypto kingpin did suffer such an attack in May 2018 resulting in a theft of $18 million of the cryptocurrency.
Hacking Attacks
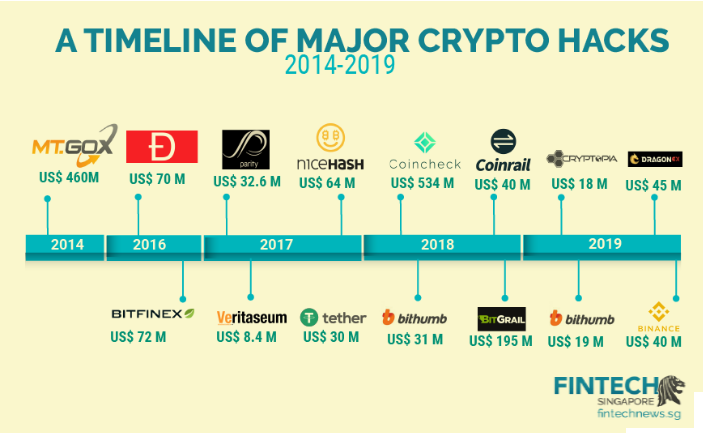
Cyber attacks on software applications that use the blockchain is one that has plagued the Cryptoverse ever since its existence & the one which has done most damage and continue to date. And the worst hit are the digital exchanges. The biggest heist that took place was in Mt. Gox – the largest bitcoin exchange at the time (2014) lost 740,000 bitcoins. Although 200,000 bitcoins were recovered, the fate of the rest remains unknown to date. The exchange went bankrupt pretty quickly. The security of most of these centralized digital exchanges remains questionable at best with the most recent hack on one of the biggest & most well-respected names in the industry, Binance which was cleaned up for $40 million. The problem remains real & is no closer to resolution.
Among others, blockchain technology is also suffering from Regulatory confusion, lack of industry consensus & technological immaturity. Unless these problems are addressed with a clear understanding of the technology at the business level, a vibrant market of commercial blockchain applications offering turn-key solutions still seems further into the future.
Email ?| Twitter ? | LinkedIn ?| StockTwits ? | Telegram ?


Weak analysis, once you went down the road of the exchanges. So you would dare say that the Federal Reserve Mint/Banks fall under this? Since there are dozens of bank robberies every single day of the year ….therefore the Fed Reserve is vulnerable? I think not!